2022 Privacy Update
September 06, 2022
If you have been following recent privacy news, you know that the pace of new state laws has not slowed from warp speed, even with the specter of a possible federal privacy law looming.
Check out our recent Gardner Law continuing legal education event and click here to view a video replay providing a rapid-fire summary on:
- New and upcoming privacy requirements in the US
- Key data transfer requirements impacting clients active in the EU or other regions
- Recent enforcement trends
- Key privacy takeaways for 2022
Common threads
It seems at times like there are more privacy laws to navigate than galaxies in the universe, but we can save ourselves some heartburn by recognizing there are common threads throughout these laws. Although described with different words and containing varying specifics, all privacy laws generally establish these principles:
- Transparency. This principle means telling people what personal data is being collected and how it will be used and shared before it is collected (think of website privacy policies, or privacy notices offered before you download a new phone app).
- Lawful or legal basis. This principle means identifying a valid and appropriate basis to collect and use personal data before collecting and using it (this could be based on consent, to meet legal requirements, to perform a contract entered with the person, among other things).
- Limited data collection. This principle means collecting and using personal data only to the extent necessary and for a legitimate purpose that is based upon a lawful basis (do not collect personal data that is “nice to have” – consider the legitimate purposes).
- Accountability (including sharing/transfer of personal data with third-parties or across borders). This principle means considering whether the recipient of the transferred data will be able to maintain appropriate security and privacy protections. Transfers should be subject to appropriate safeguards, such as contracts, risk assessments, and other controls.
- Limited retention. This principle means personal data should be kept only as long as necessary to accomplish legitimate purposes. This might be 25 years to meet regulatory requirements for clinical trial data in some cases, or in other cases certain periods necessary to address litigation hold requirements. In some cases, ”limited retention” could be not retaining a data set at all because it’s only needed at a moment in time (e.g., video streaming services). The practice of limited data retention can also reduce risks from data breaches and lower costs during discovery.
- Individual rights. This principle means personal data should be available to the individual it is about. Other rights may include ability to inspect, data portability, deletion, rectification, restrictions on processing, among others. The specifics for handling individual data subject rights requests will vary by jurisdiction, but these rights are becoming more common.
- Data security. This principle means the responsibility to maintain the confidentiality, integrity, and availability of personal data.
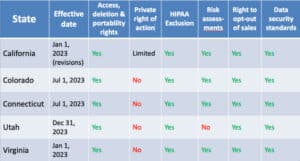
State Privacy Law Roundup
There are now five states with comprehensive privacy acts signed into law. We briefly highlight them below.
California

The California Consumer Privacy Act (“CCPA”) has been around for some time. Some highlights include:
- In effect since January 1, 2020
- Protects personal information of Californians, with some exceptions (e.g., does not apply to PHI)
- Provides many “data subject rights”: access, correction, deletion of personal data plus opt-in and opt-out rights for certain processing or sharing
- Various requirements, for example:
- Security of personal information
- Privacy notices
- Consent to “sales” of personal data
- Contract provisions for vendors
- Limited use/retention of personal data
The CCPA was amended soon after by the California Privacy Rights Act (“CPRA”):
- Most new provisions effective Jan. 1, 2023
- Updated CCPA to only apply to businesses that:
- Reach annual gross revenue of $25 million;
- Buy, receive, sell or share for commercial purposes personal information of 100,000 or more consumers, households, or devices (in California)
- Derives 50% of annual revenue from selling personal information
- Notable changes include:
- Exclusion of employee data now expires Jan. 1, 2023
- Exclusions for PHI under HIPAA
- Updates “sale” and “sharing” of personal data provision
- Clarifies clinical trial data exclusions
- Data processing with “significant risk” must be assessed and submitted to the new California Privacy Protection Agency (CCPA enforcement agency)
Here is the CCPA as amended by the CPRA.
Virginia

Some quick highlights about the Virginia Consumer Data Privacy Act (VCDPA):
- Effective January 1, 2023
- Applies to businesses that annually collect personal information on:
- 100,000 VA residents; or
- 25,000 VA residents if >50% of company revenue is from selling personal information
- Provides data subject rights, including access, correction, portability, and certain opt-out rights
- Requirements include security, privacy assessments for “high risk” processing, transparency, and contracting provisions
- Exclusions for PHI under HIPAA, employee, or B2B/“commercial” data
- Amended in 2022: “Right-to-delete” was replaced by right to opt-out from processing
Colorado

Some key notes on the Colorado Privacy Act (“CPA”) include:
- Effective July 1, 2023
- Applies to businesses that conduct business in Colorado or deliver commercial products or services targeted to residents of Colorado; and:
- Process the personal data of more than 100,000 Colorado residents in any calendar year; OR
- Sell personal data of 25,000 or more individuals
- Provides data subject rights: access, correction, portability, and deletion of personal data, plus opt-outs for targeted advertising, sale, and profiling
- Requires data security, contract provisions for vendors, assessments for “high-risk” processing
- Exclusions for PHI under HIPAA, employee, or B2B data
Utah

Utah’s business-friendly privacy law, the Utah Consumer Privacy Act (“UCPA”):
- Effective December 31, 2023
- Applies to businesses that reach annual revenues of $25 million and:
- Control or process personal data of 100,000+ Utah residents during a calendar year; OR
- Derive >50% of gross revenue from sale of personal data AND control or process personal data of 25,000+ Utah residents
- Provides rights, including transparency, access, portability, and opt-outs for sale and from targeted advertising
- Requires data security, contract provisions, privacy notices, but no risk assessments
- Exclusions for PHI under HIPAA, employee data, de-identified or “aggregated data” among other exemptions
Connecticut

The Connecticut Data Privacy Act (CDPA) is the latest state law on the books. Here are some highlights:
- Effective July 1, 2023 (most provisions)
- Applies to entities in Connecticut or producing products/services that target Connecticut residents who controlled or processed personal data in prior calendar year of at least:
- 100,000 Connecticut residents (except for payment transactions); OR
- 25,000 Connecticut residents, if the entity derived more than 25% of annual gross revenue from selling personal data
- Provides rights, including transparency, access, correction, portability, and opt-outs for sale, targeted advertising, and profiling
- Requires data minimization, limited use, security, and assessments for “high risk” processing
- Exclusions for PHI under HIPAA, employees, and B2B data
Note: Not all HIPAA exclusions are created equal, but each state law provides some exception for PHI or covered entities/business associates.
Privacy Outside of the US
We polled our Uff Da! 2022 audience and found well over half of the attendees are dealing with international data transfer challenges (uff da indeed!) That is consistent with what we are seeing as various countries and regions, notably though not exclusively the European Union (“EU”), crack down on data transfer activity. A common way this affects our US clients is when sponsoring clinical trials in EU countries or offering products in those regions.
Europe

The General Data Protection Regulation (“GDPR”) continues to raise challenges for EU-US data transfers, especially following the “Schrems II” decision by the European Court of Justice.
Highlights since Schrems II:
- New standard contractual clauses (SCCs) published by the EU are to be used solely for any new agreements since September 27, 2021
- Prior version of SCCs implemented before that date are only valid until December 27, 2022
- SCCs continue to be a key means of data transfer between EU and US; however data transfer impact assessments are needed to supplement SCCs
- US-EU data transfer agreement “in principle” was agreed to on March 25, 2022 (Do not be too optimistic just yet – data protection activists in the EU have already expressed intentions to carefully scrutinize any such agreement)
United Kingdom
Following Brexit, the United Kingdom (“UK”) has forged its own path on data protection although its laws remain (for now) very similar to the GDPR in principle and name (see UK Data Protection Act 2018). Of course, that has not kept the UK from introducing its own standard contractual agreements for international data transfer called the International Data Transfer Agreement (“IDTA”). This requirement came into effect on March 21, 2022, and the IDTA can be used as an addendum to the EU SCCs under GDPR. You can find guidance and the IDTA itself on the UK Information Commissioner’s Office (“ICO”) website.
Canada
Quebec has followed suit with its own “Bill 64” coming into effect September 2022 (though most key provisions won’t take effect until September 2023). This bill is similar to the GDPR we are familiar with but includes penalties of up to 8% of global revenue, unique cyber incident requirements (including logging of incidents, not just breaches), and heightened consent standards. It also includes cross border transfer requirements.
China
China’s Personal Information Protection Law (PIPL) (for-reference-only English translation available here) became effective November 1, 2021. This law is intended to apply to companies that process information about individuals in China, carrying penalties up to 5% global revenue or $7.7m (whichever is greater). Additionally, this law requires multi-layer consent mechanisms for certain processing activities, data breach response requirements, data mapping, as well as (released since the event) standard contractual clauses for international data transfers for certain types of transfers, among other requirements.
Cybersecurity Update
U.S. Federal Agency Activity
The federal government continues to find ways to address lax cybersecurity. We have the Securities Exchange Commission (“SEC”) proposing rules on cybersecurity for public companies:
...Current reporting about material cybersecurity incidents and periodic reporting to provide updates about previously reported cybersecurity incidents. The proposal also would require periodic reporting about a registrant’s policies and procedures to identify and manage cybersecurity risks; the registrant’s board of directors' oversight of cybersecurity risk; and management’s role and expertise in assessing and managing cybersecurity risk and implementing cybersecurity policies and procedures. The proposal further would require annual reporting or certain proxy disclosure about the board of directors’ cybersecurity expertise, if any.
The Federal Trade Commission (“FTC”) brought enforcement actions throughout 2021 against a variety of companies for alleged false and deceptive trade practices and issued a new policy statement in January 2021 clarifying the FTC’s Health Breach Notification Rule’s application to health apps. (Since the time of the presentation, the FTC has also issued an Advanced Notice of Proposed Rule Making on Commercial Surveillance and Data Security).
In 2021, the Department of Justice (“DOJ”) announced a new initiative to use the False Claims Act (“FCA”) to prosecute fraud by federal contractors tied to cybersecurity requirements. The first enforcement action under this initiative was against Comprehensive Health Services (“CHS”), where the government alleged CHS maintained patient records at government-run facilities on unsecured, accessible drives rather than the secure Electronic Health Record system paid for by the government.
Enforcement Update
EU privacy enforcement continues, with the French DPA leveling fines of €210m for violations of France’s “cookie legislation” that took effect in March 2021. Austrian and French DPAs also determined that two website operators’ use of Google Analytics was violative.
Click here to watch Paul Rothermel, Associate Attorney, Gardner Law, share more about the latest privacy requirements that impact drug and device makers.
Have questions? Contact us.
Information provided on this website is not legal advice. Communications sent to or from this site do not establish an attorney-client relationship. © 2022 Gardner Law. All Rights Reserved.